Cloud Security Tips: 10 Essential Strategies to Fortify Your Data in 2024
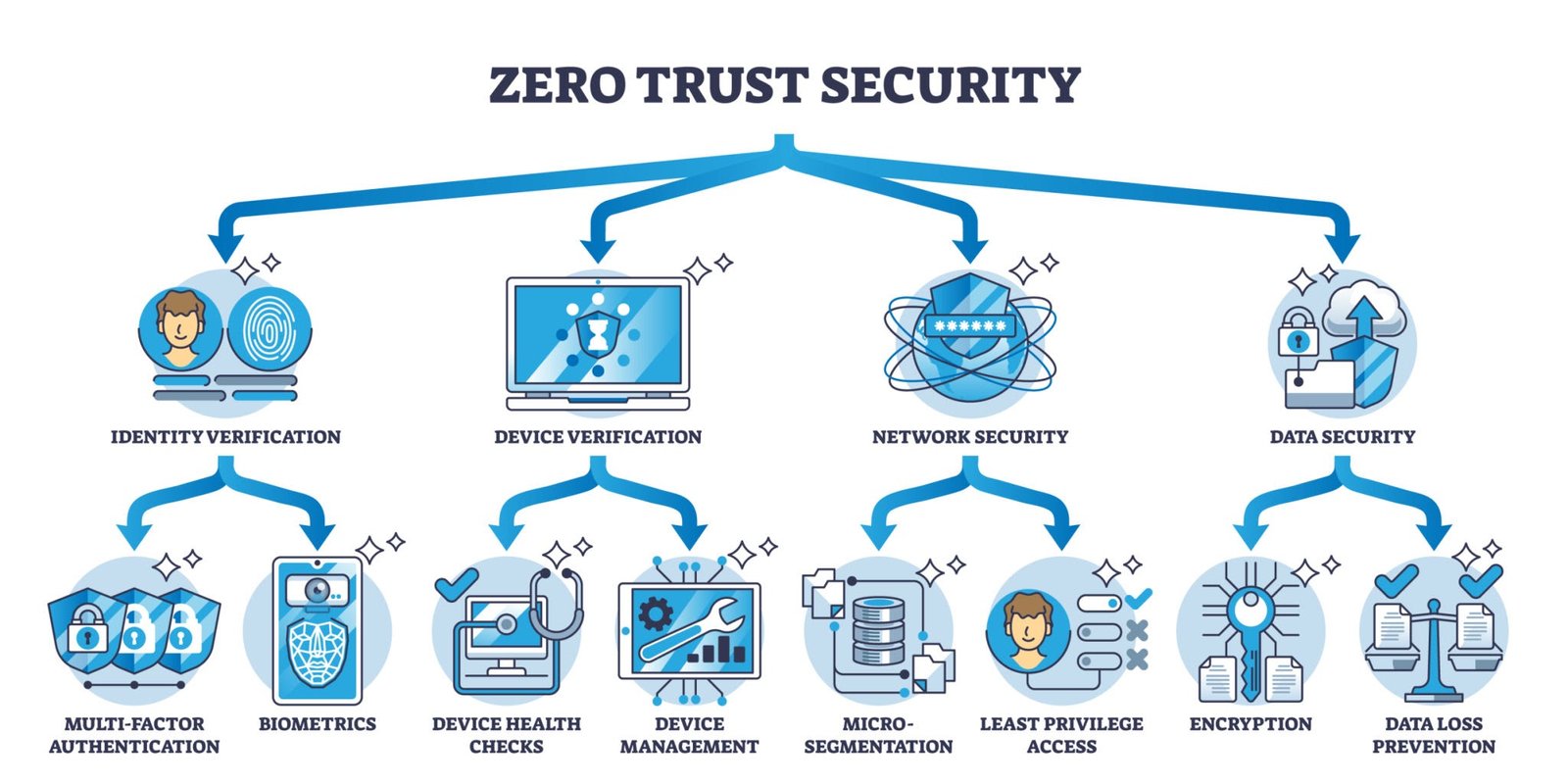
Table of Contents
Introduction: A Shared Responsibility Regarding Cloud Safety
The Non-Negotiable: Foundational Identity & Access Management
Encrypt Everything: Data At Rest And Data In Motion
Visibility Is Your Superpower: The Importance Of Monitoring
Building For The Future: Security by Design
The Human Firewall: Training And Culture
Proactive Defense: Threat And Vulnerability Management
Planning For The Inevitable: Cloud Incident Response
Choosing Your Partner: Third-Party Risk And CSP Due Diligence
Conclusion: Security Is A Never-Ending Journey
1. Introduction: A Shared Responsibility Regarding Cloud Safety
First to clear up a common misconception: moving to the cloud doesn’t mean you’re outsourcing your security. What you’re moving into is simply a shared responsibility model. Your cloud service provider (AWS, Azure, Google Cloud, etc.) secures the underlying infrastructure (physical data centers, hardware, hypervisor), but you are responsible for obtaining everything you place on that infrastructure. This includes your data, applications, your identities, and your network configurations. The cloud is a powerful tool, but it comes with a new set of vulnerabilities and a new set of attack surfaces. Thus, following good cloud security practices is not only an issue for the IT department but also a concern for the entire organization.
This guide covers the top 10 strategies for elevating your cloud security from the basics to the next level by incorporating a proactive approach into your security posture.
2. The Non-Negotiable: Foundational Identity and Access Management (IAM)
If there is one tip from this list that you should consider the most important, it should be this one: Identity is the new perimeter. The castle-and-moat theory doesn’t work anymore, especially when data can be accessed from anywhere. The most important thing you can do for your cloud security is to ensure that you have control over who can access your data and resources.
Implementing the principle of least privilege is a best practice that all organizations should follow. Each user, service account, and application should be given the least amount of permissions necessary to accomplish their tasks. A marketing app should not have access to financial records, and a developer should not have database admin rights. These permissions should be reviewed and cleaned up on a regular basis.
Implementing Mandated Multi-Factor Authentication (MFA) may be the most important thing you can do for your security posture. Passwords can be easily compromised, and MFA is a much more secure form of authentication that will prevent the majority of automated attacks. MFA should be required for all accounts, and especially for admin accounts. This one activity prevents most attacks.
Use Single Sign-On (SSO) and Federated Identity: Using SSO with an Identity Provider (like Okta, Azure AD) helps to minimize password fatigue, enhances offboarding, and puts everything you need to manage accessibility of services on a single interface. Identity Control should be centralized.
These IAM-focused cloud security tips help mitigate breaches via credential compromise, which continues to be one of the major causes of data loss.
3. Encrypt Everything: Data at Rest and Data in Use
Think of data encryption as a way of converting your valuable information, your data, to a proprietary and obscure dialect. Even if an attacker is able to navigate passed every other line of defense, without the encryption key, the data is useless.
Data at Rest: Ensure all sensitive data stored in the cloud databases, object storage (like S3 buckets) and disks of virtual machines is encrypted using strong industry standard algorithms (AES-256). Make sure it’s turned on since most cloud storage providers offer it by default.
Data in Transit: Data that is in the movement phase should always stay encrypted with TLS and/or SSL. Secured communications via HTTPS should be mandatory, with no permitted exceptions of unencrypted transfers.
Use your Encryption Keys Wisely. Encryption keys are the building blocks of any encryption system; thus, proper encryption key management is important. In the case of very sensitive data, instead of using the cloud provider encryption key management services (such as AWS KMS, Azure Key Vault), consider managing your encryption keys. This ensures that only you have access to your sensitive data, as your cloud provider will not have access to your encryption keys. Ensuring you have full control of your encryption keys is an important aspect of your cloud security strategy.
Ensuring Confidentiality Implementing the cloud security recommendations that have been addressed in the previous sections will help you to meet some of the main cloud security compliance requirements, including confidentiality (GDPR, HIPAA, etc.). There are quite a few security standards that have secrecy as a key principle; protecting sensitive data should not go ignored. Controlling access to sensitive data is also a key aspect of confidentiality.
4. Visibility Is Your Superpower: Active Monitoring Of Threats.
Visibility is your superpower. If you cannot see a problem, then you cannot solve the problem. In a cloud environment where resources can be provisioned with an API call, and are very dynamic, the less control, and thus, you have an unprecedented risk. Zero Trust architecture further exacerbates the risk; therefore means no one should be trusted. Continuous Active Monitoring is Key.
Visibility and Active Monitoring Of Your Cloud Environment.
While Cloud Monitoring is an important concept to grasp, you can be certain that every one of your users has access to the cloud services, and the resources you provision in a very dynamic manner, and of course, cloud providers are very dynamic and responsive, so your resources can use an API to provision. Centralized Cloud Service Monitoring is important to any organization; every organization should have an ordered approach. The C.A.D.E.S. approach. Centralized Logging Policy must be in place – Across your organization, for every virtualization Computed Resource (VCRs), where a cloud provider virtualizes all the resources to a single server, you should have a centralized logging resource, such as a virtual resource, where all the data is collected and then deduplicated. An example of Leap is where you have a free resource, such as a cloud virtual machine (VM), which is a single physical computer where cloud providers virtualize and then offer to users. In terms of dedicated cloud virtual machines, log data in at the virtual machine level.
Enable Comprehensive Logging of every Cloud Resource: It is critical to have implemented a centralized logging system by extending cloud logging for the following: User (who has access to management level and can control resources), Network, and System Layer. Centralized Logging means that every cloud resource: user, network, system, etc, has a logging strategy.
Enable Comprehensive User Activity Logging: It is important to have a logging strategy for centralized user activity logging that covers:
Centralized System Activity Logging: It is also important to have a logging strategy for centralized system activity logging that covers:
Network Activity System Layer → System Activity The Network Layer is very important, especially in system controls, and the system activity logging layer.
So, where is the system activity logging layer?
It is very important to have in place a network system activity logging in every system layer, documenting system activity logging.
Enable Comprehensive User Activity Logging: to log.
Automated Alerting Systems: ‘Logs are data, alerts are intelligence’: to extract intelligence from logging data, it is important to automate logging alerts so that the alerting systems can respond to logging data.
Automated alerting systems need to be implemented to extract intelligence from your logging data and process it. Automated alerts should be set to process log data.
Automated Alerting Systems: ‘Logs are data, alerts are intelligence’: to extract intelligence from logging data, it is important to automate logging alerts so that the alerting systems can respond to logging data.
Conduct Regular Audits: Consistently analyze your logs and configurations on a weekly and monthly basis. Determine if there is any deviation from your security baselines. Tools like AWS Config and Azure Policy can automate compliance investigations.
If you start managing your security proactively (instead of reactively), you will experience predictive security and fully appreciate the value of this tip.
5. Building For The Future: Security by Design
Security should be baked into your cloud environment from initial architecture, rather than being incorporated as an afterthought.
Network Segmentation: Virtual Private Clouds (VPCs) and subnets can be used to segment your network. Your publicly accessible web servers will be in a different subnet (with strict controls) than your backend databases, which should not have public internet access at all.
Implement Security Groups & NACLs: Think of these as precise, stateful firewalls for your cloud resources. Therefore, be as restrictive as possible by limiting the allowed ports and source IPs. For example, a database should only accept connections from the specific application server that is intended to access it.
Embrace Zero Trust Network Access (ZTNA): Stop using the “trust but verify” model since it is outdated. Instead, ZTNA approaches access with the mindset of “never trust, always verify.” Self-contained access requests are always authenticated, authorized, encrypted, and validated before any access is granted, regardless of the user’s location.
With these tips, you’ll be able to focus your attention on a few areas to lessen your risk and focus on the areas to breach.
6. The Human Firewall: Training and Culture
A company can be taken down easily by one employee who has fallen victim to a phishing scam. To a company, an employee is one of the weakest members. To an employee, a company is one of the most powerful.
Constant Security Awareness Training: Get rid of the old annual compliance training system. Make the training active by using micro-lessons on phishing and social engineering. Get employees ready for the training through a phishing simulation.
Make Clear Cloud Expenditure Policies: Employees will engage with cloud software services. Help employees by setting clear ground rules for Service Cloud data and how to report a suspicious email.
Encourage “See Something, Say Something”: Make it the employee’s job to be a security soldier. They should be able to report incidents without punishment.
Investing in human-centric cloud security technology will create an organizational culture of resilience. This type of culture is extremely difficult to create with technology alone.
7. Proactive Defense: Threat Anticipation and Weak Point Prevention
Not receiving an alert is a defensive measure. Proactive security implies the search for threats that have not set off an alarm.
Vulnerability Management: Don’t forget to run a vulnerability scan on your cloud workloads. Are there containers and dependencies? Make use of both agent and agentless scanners and prioritize responding to critical and high-severity flaws based on real-world exploitability, not a CVSS score.
Threat Hunting: Security teams need to get ahead of the game and actively interrogate their logs and their environment for Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs) of Advanced Persistent Threats (APTs) and look for appropriate rule evasion.
Penetration Testing and Red Teaming: Consistently, enlist the aid of ethical hackers to evaluate your cloud environment. A simulated attack on your services gives a more accurate real-world perspective of your environment’s self-defenses and of your incident response readiness.
These more advanced cloud security tips ‘move left’ with your security operations, anticipating incoming attacks.
8. Planning for the Inevitable: Incident Response in the Cloud.
Have a breach response plan ready, understanding that a breach will occur. The main line in the sand separating a moderate incident from wildfire headlines boils down to your preparations.
Have a Cloud-Specific Us-IR plan: Incident response plans from an on-premises environment won’t translate. This plan will need to account for cloud-specific services, evidence collection from cloud APIs, and protocols for communicating with your Cloud Service Provider’s security team.
Practice with Tabletop Exercises: Regularly run breach scenario exercises with major stakeholders (IT, legal, PR, executive leadership). Who is the Incident Commander? How do you maintain forensic evidence in an ephemeral cloud environment? How do you preserve the ability to communicate?
Automated Action: Author in advance a set of containment actions that you must preapprove and script. For example, if a workload is determined to be compromised, automatically quarantine it from the network or shut it down to prevent lateral movement.
These preparative cloud security tips make sure that when the pressure is on, your team will be able to function from a rehearsed playbook.
9. Choosing your Partner: Third Party Risk and CSP Due Diligence
Your security is only as strong as the weakest link in your supply chain, and that includes the apps and services you connect to your cloud environment.
Vet your Cloud Service Provider (CSP): Know their security compliance certifications (SOC 2, ISO 27001, etc.). Assess their shared responsibility model against your own, and make sure you know where their responsibility ends and yours begins.
Check Third-party Apps: Before integrating a SaaS app or marketplace tool, conduct a security review. What kind of data will it access? What is their security posture? How do they handle your data?
Control API Security: There is an API for every integration. Protect these endpoints with strong authentication (OAuth, API keys) and monitor their usage for deviations. An API key is as risky as a password, and it can be compromised.
With these partnership-centered cloud security strategies, you can extend your security governance beyond your immediate control.
10. Conclusion: Security as a Continuous Journey
Moving to the cloud the first time isn’t just a one-time migration; it’s a transformation into a new operational model. Likewise, cloud security isn’t just a one-time project. It’s a continuing cycle of improvement. The cloud security tips that were already mentioned, such as mastering IAM, encryption, and incident response, create a well-rounded framework. Begin with the base level tips, such as the enforcement of MFA and least privilege. Then continue to progressively advance your program with better monitoring, proactive hunting, and thorough architecture reviews. In the digital world, the state of your cloud security is a reflection of your business adaptability, customer confidence, and profit. Make it a top priority, keep investing, and continue to stay enlightened. Your data’s safety depends on it.
You may also read itbigbash.